Introduction to the TCP/IP Protocol Framework
Alright, time to dive into one of the most important parts of cybersecurity.
NETWORKING! This blog will teach about network basics of TCP/IP and OSI
models, DNS, DHCP, as well as switching and routing concepts, IP addressing,
NAT, packet sniffing and finally, structures and vulnerabilities of key
databases including SQL, CouchDB, Oracle and MongoDB. Let's get started!
Stateless Inspection
To start off the topic of networking let's discuss what firewalls are and how
they utilize stateless and stateful inspection, then compare stateless
firewalls to stateful firewalls. According to Cisco (one of the leading
companies in network technology) firewalls are
"A firewall is a network security device that monitors incoming and
outgoing network traffic and decides whether to allow or block specific
traffic based on a defined set of security rules. Firewalls have been a
first line of defense in network security for over 25 years. They establish
a barrier between secured and controlled internal networks that can be
trusted and untrusted outside networks, such as the Internet. A firewall can
be hardware, software, or both.". Now that we know what a firewall is, let's dig a little deeper into how
firewalls filter incoming and outgoing network traffic stateless and stateful
inspection. Regular routers and some firewalls use the stateless way of
filtering packets, this means the firewall inspects each packet without any
knowledge of previous packets, the firewall will inspect the destination and
source address of the packet and then block or restrict addressess that are
deemed untrusted. There may also be an Access Control List rule (ACL) that
will determine weather the source addess and destination port of the packet is
allowed on the network or if the destination address is allowed to be accessed
or not. A few use cases for stateless inspection include:
Protecting routing engine resources.Controlling traffic going in or out your organization.Troubleshooting purposes.Control traffic routing (through the use of routing instances).Perform QoS/CoS (marking the traffic).Stateful Inspection
Heading back over to Cisco, a Stateful Inspection is
"Now thought of as a “traditional” firewall, a stateful inspection firewall
allows or blocks traffic based on state, port, and protocol. It monitors all
activity from the opening of a connection until it is closed. Filtering
decisions are made based on both administrator-defined rules as well as
context, which refers to using information from previous connections and
packets belonging to the same connection.". In some cases there can be a stateless and stateful inspection, the
stateless inspection is going to be performed first and then will be followed
up by an evaluation of the stateful data. Now that we know about stateless and
stateful inspections what are the pros and cons of each method ? Below is a
list of the pros and cons of each inspection method courtesy of
CDW.
IDS and IPS Systems
Now that we've talked about firewalls and the different types of firewalls,
let's talk a little about 2 types of firewall filters. Intrusion Detection and
Intrusion Prevention Systems. An Intrusion Detection System (IDS)
"is a network security technology originally built for detecting
vulnerability exploits against a target application or computer.". Intrusion Prevention Systems (IPS)
"extended IDS solutions by adding the ability to block threats in addition
to detecting them and has become the dominant deployment option for IDS/IPS
technologies.".
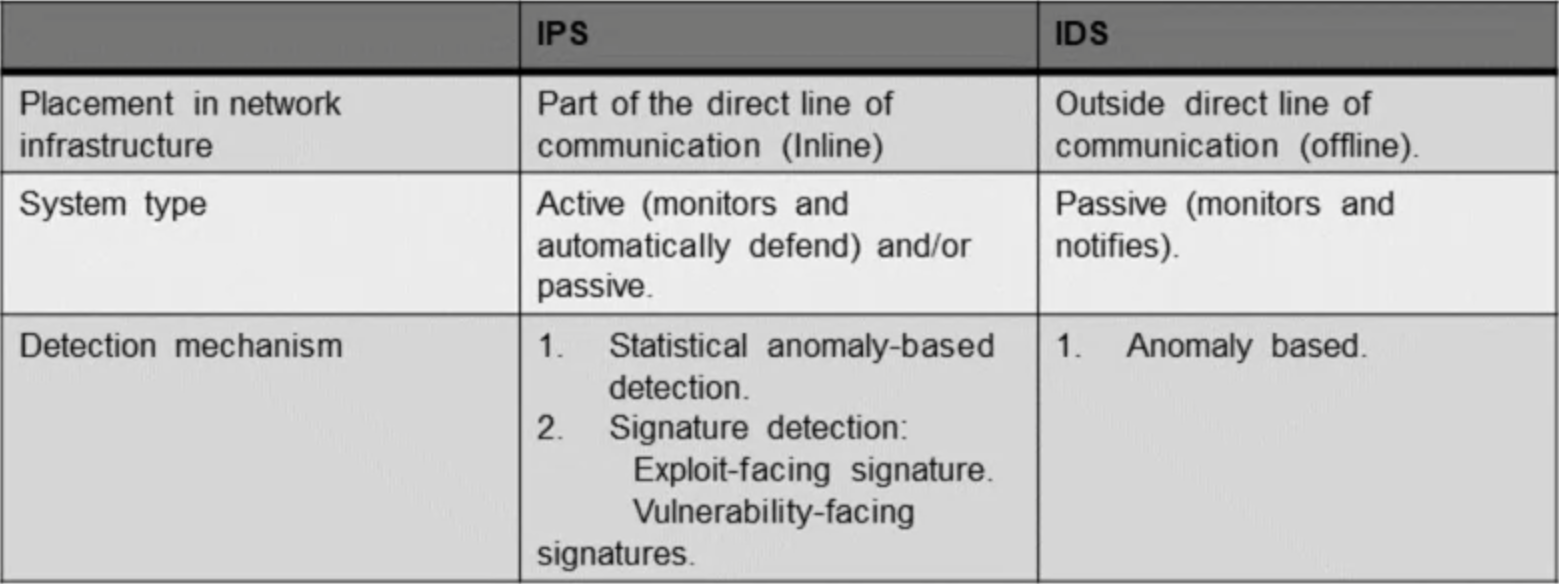
Intrusion Detection Systems
An IDS needs to only detect threats on a network, because the IDS only detects
threats and reports it's finds to an administrator. It is placed outside of
the real-time communication path of the sender and receiver of information,
which makes it a passive system. Due to the IDS not keeping up with real-time
communication it will often take advantage of a TAP or SPAN port to analyze a
copy of the inline network traffic stream. This ensures that the IDS does not
impact inline network performance. Unfortunately due to the nature of IDS
solutions, they lack the ability to prevent a detected exploit from taking
over the system. Attackers are capable of quickly exploiting vulnerabilities
once they've infiltrated the network. Rendering the IDS useless.
Intrusion Prevention Systems
IPS on the other hand, has the ability to block threats along with detecting
them. The IPS often sits directly behind the firewall and adds a layer of
analysis that actively searches for dangerous content. The IPS sites inline or
in the direct path of communication of the sender and receiver and takes
automated actions on all traffic flows that enter the network. The actions
performed by an IPS include:
Sending an alarm to the administrator(as would be seen in an IDS)Dropping the malicious packetsBlocking traffic from the source addressResetting the connectionSince the IPS works as an inline security component, it is crucial that the
IPS works fast and efficiently to avoid degrading network performance as
well as detect and respond to exploits accurately since exploits can happen
in near real time. When it comes to detection methods IPS has a number of
different detection methods but signiture-base and stistical anomaly-based
are the two dominant methods. Signature-based detection
"is based on a dictionary of uniquely identifiable patterns (or
signatures) in the code of each exploit. As an exploit is discovered, its
signature is recorded and stored in a continuously growing dictionary of
signatures. Signature detection for IPS breaks down into two types:"
Exploit-facing signatures identify individual exploits by triggering on
the unique patterns of a particular exploit attempt. The IPS can
identify specific exploits by finding a match with an exploit-facing
signature in the traffic stream
Vulnerability-facing signatures are broader signatures that target the
underlying vulnerability in the system that is being targeted. These
signatures allow networks to be protected from variants of an exploit
that may not have been directly observed in the wild, but also raise the
risk of false positives.
Statistical anomaly detection
"takes samples of network traffic at random and compares them to a
pre-calculated baseline performance level. When the sample of network
traffic activity is outside the parameters of baseline performance, the
IPS takes action to handle the situation."
Network Address Translation
NAT or Network Address Translation is essentially a method of converting a
private IP address to a public IP address when connecting to the Internet. NAT
remaps the IP address by modifying information in the IP datagram packet
headers as they transit across a traffic routing device. This is just a
summerized version of what NAT is but you can read more about it through a FAQ
form on CISCO's website
Network Address Translation (NAT) FAQ. Below is a diagram of a Juniper NAT router and 4 key facts about NAT.
Static, Dynamic, and PAT Address
Static NAT- Allows one-to-one mapping between local and global addresses.
Dynamic NAT- A technique in where multiple public IP addresses are mapped to
a local IP address to be used.
Port Address Translation (PAT) - Maps multiple local IP address to a single
public address to conserve IP addresses. This method is often referred to as
"Overloading". By using overloading, thousands of users can be
connected to the Internet by using only one real public IP address.
I am actively looking for work, feel free to connect with me and lets talk business. Also feedback is appreciated! Thank you!
Connect With Me 😊




Introduction to the TCP/IP Protocol Framework
Alright, time to dive into one of the most important parts of cybersecurity. NETWORKING! This blog will teach about network basics of TCP/IP and OSI models, DNS, DHCP, as well as switching and routing concepts, IP addressing, NAT, packet sniffing and finally, structures and vulnerabilities of key databases including SQL, CouchDB, Oracle and MongoDB. Let's get started!
Stateless Inspection
To start off the topic of networking let's discuss what firewalls are and how they utilize stateless and stateful inspection, then compare stateless firewalls to stateful firewalls. According to Cisco (one of the leading companies in network technology) firewalls are "A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Firewalls have been a first line of defense in network security for over 25 years. They establish a barrier between secured and controlled internal networks that can be trusted and untrusted outside networks, such as the Internet. A firewall can be hardware, software, or both.". Now that we know what a firewall is, let's dig a little deeper into how firewalls filter incoming and outgoing network traffic stateless and stateful inspection. Regular routers and some firewalls use the stateless way of filtering packets, this means the firewall inspects each packet without any knowledge of previous packets, the firewall will inspect the destination and source address of the packet and then block or restrict addressess that are deemed untrusted. There may also be an Access Control List rule (ACL) that will determine weather the source addess and destination port of the packet is allowed on the network or if the destination address is allowed to be accessed or not. A few use cases for stateless inspection include:
Stateful Inspection
Heading back over to Cisco, a Stateful Inspection is "Now thought of as a “traditional” firewall, a stateful inspection firewall allows or blocks traffic based on state, port, and protocol. It monitors all activity from the opening of a connection until it is closed. Filtering decisions are made based on both administrator-defined rules as well as context, which refers to using information from previous connections and packets belonging to the same connection.". In some cases there can be a stateless and stateful inspection, the stateless inspection is going to be performed first and then will be followed up by an evaluation of the stateful data. Now that we know about stateless and stateful inspections what are the pros and cons of each method ? Below is a list of the pros and cons of each inspection method courtesy of CDW.
IDS and IPS Systems
Now that we've talked about firewalls and the different types of firewalls, let's talk a little about 2 types of firewall filters. Intrusion Detection and Intrusion Prevention Systems. An Intrusion Detection System (IDS) "is a network security technology originally built for detecting vulnerability exploits against a target application or computer.". Intrusion Prevention Systems (IPS) "extended IDS solutions by adding the ability to block threats in addition to detecting them and has become the dominant deployment option for IDS/IPS technologies.".
Intrusion Detection Systems
An IDS needs to only detect threats on a network, because the IDS only detects threats and reports it's finds to an administrator. It is placed outside of the real-time communication path of the sender and receiver of information, which makes it a passive system. Due to the IDS not keeping up with real-time communication it will often take advantage of a TAP or SPAN port to analyze a copy of the inline network traffic stream. This ensures that the IDS does not impact inline network performance. Unfortunately due to the nature of IDS solutions, they lack the ability to prevent a detected exploit from taking over the system. Attackers are capable of quickly exploiting vulnerabilities once they've infiltrated the network. Rendering the IDS useless.
Intrusion Prevention Systems
IPS on the other hand, has the ability to block threats along with detecting them. The IPS often sits directly behind the firewall and adds a layer of analysis that actively searches for dangerous content. The IPS sites inline or in the direct path of communication of the sender and receiver and takes automated actions on all traffic flows that enter the network. The actions performed by an IPS include:
Since the IPS works as an inline security component, it is crucial that the IPS works fast and efficiently to avoid degrading network performance as well as detect and respond to exploits accurately since exploits can happen in near real time. When it comes to detection methods IPS has a number of different detection methods but signiture-base and stistical anomaly-based are the two dominant methods. Signature-based detection "is based on a dictionary of uniquely identifiable patterns (or signatures) in the code of each exploit. As an exploit is discovered, its signature is recorded and stored in a continuously growing dictionary of signatures. Signature detection for IPS breaks down into two types:"
Network Address Translation
NAT or Network Address Translation is essentially a method of converting a private IP address to a public IP address when connecting to the Internet. NAT remaps the IP address by modifying information in the IP datagram packet headers as they transit across a traffic routing device. This is just a summerized version of what NAT is but you can read more about it through a FAQ form on CISCO's website Network Address Translation (NAT) FAQ. Below is a diagram of a Juniper NAT router and 4 key facts about NAT.
Static, Dynamic, and PAT Address
I am actively looking for work, feel free to connect with me and lets talk business. Also feedback is appreciated! Thank you!
Connect With Me 😊